Cryptographic Protection schemes are as old as the hills. The need to protect sensitive information—especially financial transactions—securely is an ever-evolving cat-and-mouse game. Passwords, account verifications, transaction security, and even encrypted currency data are meant to allow people (and machines) that don’t trust each other to do business.
Blockchain, like any not fully understood technology, has its critics as well as disciples. In this posting, we will examine how secure blockchain really is.
Blockchain Shares Massive Amounts of Data
The underlying belief that blockchain is a secure technology stems from the massively shared data containing every transaction ever made in ledgers stored redundantly on distributed networked nodes. Transactions are validated and combined in blocks that chain to previous blocks in a chain. The miners who own and control the nodes profit by adding new blocks to the massively distributed and redundant ledgers.
Blockchain Security Methods
The key to making this work is the trust placed in the fingerprint. This fingerprint is designed to be unique to each block. The protocol that is supposed to agree on the shared history is called consensus protocol. Based on a hash-code generation technique, the fingerprint is a compute-intensive string created and posted as a proof-of-work seal. Here, it is easy to verify that a hash code matches the block’s content so each node can rather effortlessly verify and update their copy of the blockchain with the new block (Figure 1).
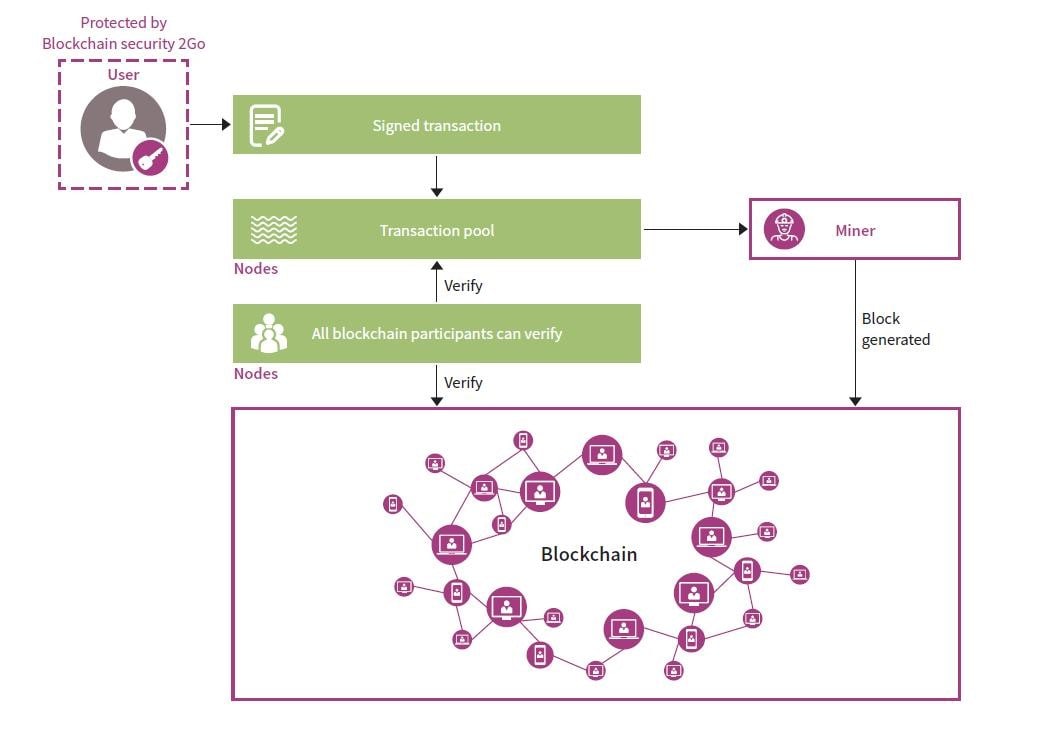
Figure 1: It might seem that Blockchain processing nodes are too complex for the average developer or designer to implement easily, but development kits such as the Infineon Blockchain Starter Kit teach the technology and enable designers to create security, authentication, and verification nodes. (Source: InfineonTechnologies)
Any attempts to alter the block require a new compute-intensive seal to be generated simultaneously at multiple nodes in real-time fast enough so that no new blocks will have been added to the chain. In other words, it would require computers faster than all the other nodes on the network to add or modify blocks that don’t conflict with the other nodes. In theory, with a level playing field, this sounds pretty good. But in practice, this is a new cat-and-mouse game evolving.
Subverting the Blockchain
Researchers at MIT and Cornell University, for example, have demonstrated that even using secure tools, the result isn’t always secure. They can also attack the distributed nodes by acting selfishly to subvert the blockchain by making nodes waste computing power on unnecessary, redundant tasks. This allows a weaker computer to seem more powerful. While hacking the entire network at one time seems unlikely, it is easier to hijack a single node’s communications, allowing it to manipulate or insert false data, waste time doing calculations it doesn’t need to do, or confirming fake transactions.
This is not just theory talking. Newly emerging virtual current organizations that use blockchain technology have been robbed, such as the decentralized autonomous organization (DAO) in 2016, for example. Permission-based systems also bring in their own vulnerabilities, such as allowing node owners to make changes that the rest of the network doesn’t know about or agree with. A virtual screen door of possibilities can farkle (or function and sparkle) the network. This causes the community to force software updates, or hard fork, to recover money. In essence, the approach to centralize makes one target, but the characteristics of distributed compute architecture make any weak computer an easier target.
Looking Forward
Regardless of how securely a system is designed, each has its vulnerabilities. Blockchain,continues to evolve and remains a favored option to combat cybersecurity challenges.







