Infineon Technologies AG provides its OPTIGA Trust M security solution to Thistle Technologies for its new cryptographic protection for on-device AI models to its security software platform for embedded computing products based on the Linux operating system (OS) or on a microcontroller. The new capabilities in the Thistle Security Platform for Devices, along with Infineon OPTIGA Trust M security solution as tamper-resistant hardware-based root-of-trust, protect the valuable intellectual property (IP) in the AI models deployed in edge AI applications, and in the training data sets on which they are based.
The Thistle Security Platform for Devices that includes the Infineon OPTIGA Trust M security solution, provides ready-made, cloud-managed security components which integrate seamlessly into Linux OS-based devices and microcontrollers. Instead of building and maintaining a one-off cybersecurity stack, OEMs can deploy a proven, continuously updated foundation in hours, and scale it across large, heterogeneous fleets of devices. The Security Platform enables both secured boot and over-the-air (OTA) updating, and is compatible with a broad range of microprocessors, systems-on-chip (SoCs) and microcontrollers. Infineon OPTIGA Trust M security controller enables secured key provisioning, tamper-resistant key storage, and efficient cryptographic operations for encryption and decryption, taking care that only trusted, authenticated, and verified AI models are deployed in edge AI applications.
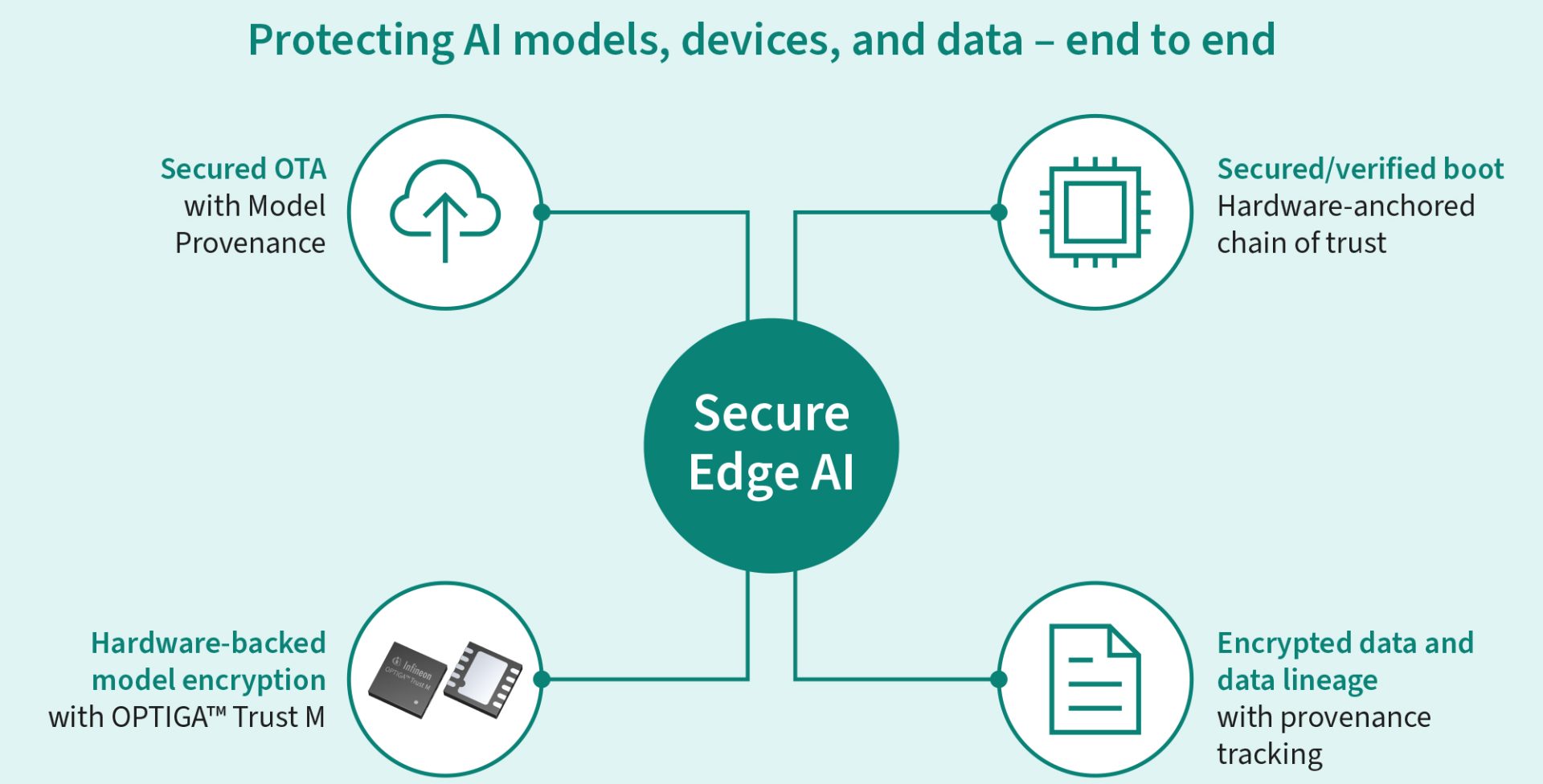
Thistle has extended its solution to include built-in protection for on-device AI models and data, using cryptographic keys stored in Infineon’s tamper-resistant security controllers, OPTIGA Trust M. The three key features of the new Thistle Secure Edge AI solution are:
- Hardware-backed model encryption – AI model encryption key is secured by OPTIGA Trust M security solution. Each device has a unique AES 256-bit key securely stored in OPTIGA Trust M, which is used to secure the AI Model encryption key. This means that the AES key is used for encryption and decryption inside the OPTIGA Trust M only. Even if a device is lost, decommissioned, or disassembled, the manufacturer’s IP embedded in the model is still efficiently protected. At launch, this feature is enabled on the Infineon OPTIGA Trust M security solution.
- Secured model provenance – in OTA updates, the Thistle platform enables cryptographically signed, tamper-evident delivery of AI models and firmware directly from the training platform to the device, taking care that every installed instance of a model can be traced and verified.
- Signed data and data lineage – device-generated or collected data can be signed on-device and tagged with provenance metadata. This means that downstream systems which might use the data to train or refine AI models can check the provenance of the data, and of the version of the model that the device was running when it generated the data.
Animesh Ranjan, Head of Partnerships & Ecosystem at Infineon says: “At Infineon, we are pleased to expand our collaboration with Thistle Technologies to deliver stronger protection for AI models running at the edge. By combining the OPTIGA Trust M security solution with the Thistle Security Platform, we enable device makers to safeguard their AI with hardware-anchored security that is both practical and scalable.”
Window Snyder, Chief Executive Officer of Thistle Technologies, says: “It is always our goal to make robust security capabilities accessible for device makers. With Infineon’s OPTIGA Trust M and the Thistle Security Platform, manufacturers can protect AI models and data with proven cryptography and deploy at scale quickly. Together we give customers a straightforward way to ship devices that can securely verify, encrypt, and update AI models.”